Neues Passwort-Problem in MacOS High Sierra
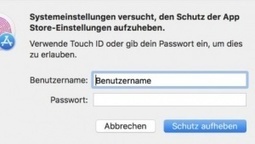
MacOS High Sierra hat erneut ein Problem: Nun ist bekannt geworden, dass die Einstellungen für den eingebauten App Store ohne korrektes Passwort geändert werden können.
In der aktuellen Version von MacOS High Sierra können die Einstellungen im App-Store-Menü in den Systemeinstellungen mit einem beliebigen Passwort geändert werden. Dies zeigt ein Bugreport auf Open Radar. Die Sicherheitslücke ist indes nicht so gravierend wie die passwortlose Root-Anmeldung unter MacOS High Sierra und erfordert einen Administrator-Account.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security



 Your new post is loading...
Your new post is loading...






Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security